Tokyo, midday on a Friday. My phone kept buzzing during my customer meeting. The day was a workday, a day of travel and the day a personal property purchase was due to settle. Little did I know it was also the day I was the target of a “port-out” scam.
In the few minutes I had between one meeting and the next, I glanced at my phone trying to keep pace with solicitor updates regarding my property transaction finalizing. Amidst the deluge of notifications my phone was providing, one thing I quickly dismissed were two verification SMS codes sent by my telco provider that I hadn’t asked for and didn’t give a second thought to:

Then I saw something I remember our cybersecurity expert warning us about
Just over two hours later, I received the following text from my telco (telco name and my details are redacted out purposefully):
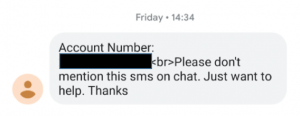
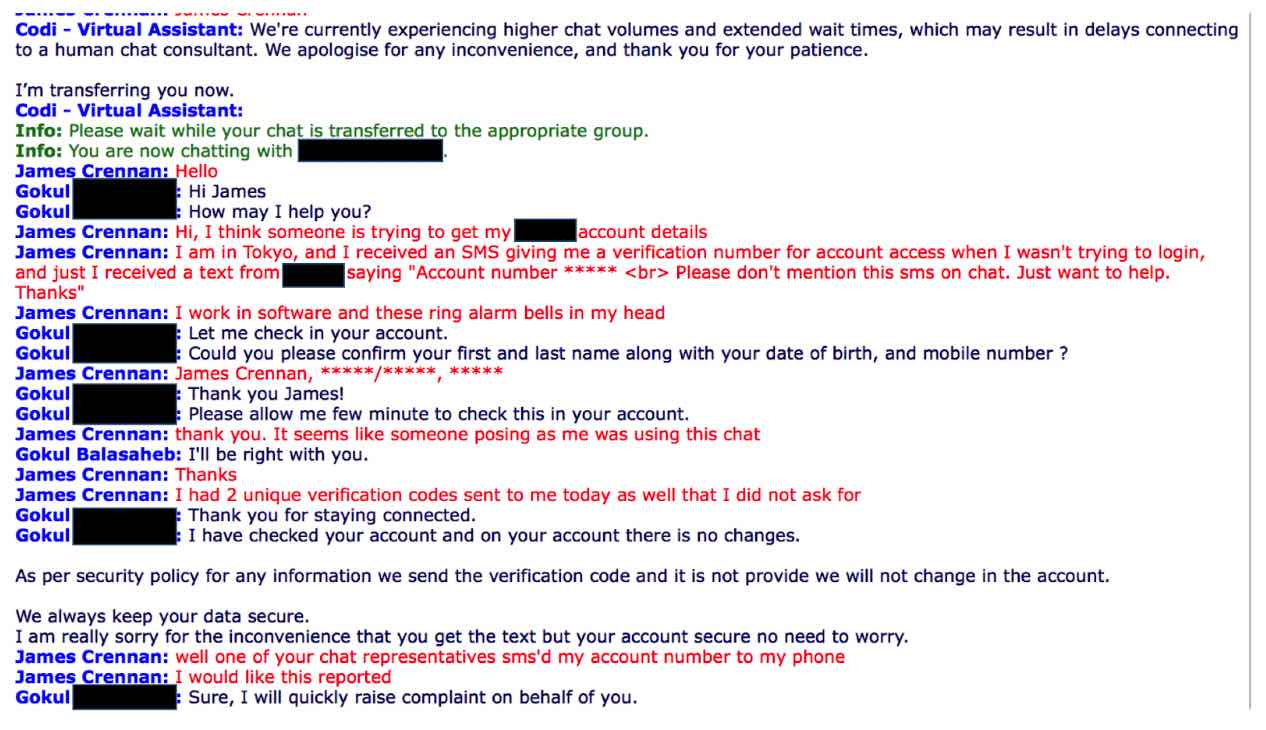
Needless to say, this is something that would set alarm bells ringing for anyone. I instantly think that someone is posing as me, requesting information they shouldn’t and somehow creating enough sympathy or compassion in a chat representative to make them breach company policy and reveal my account number via SMS. There was likely some additional information checks needed to complete a verification process in the event than SMS verification is not possible, such as saying your phone has been stolen. And, well, this SMS is evidence that someone was seeking that extra information to add one more piece to the data puzzle. All of a sudden the two previous SMS verification codes didn’t seem so innocent.
I started trying to take action
I was still in possession of my phone number at this point, and proceeded to get in contact with my phone company via online chat. At the same time, I tried logging into my online account, to be denied with a password I either didn’t remember or had changed. I requested a password reset and started a chat with the support agent. The first part of the conversation is below:
As you can see, I went through their verification process easily and they assured me that nothing had been changed in my account, “I have checked your account and on your account there is no changes…. I am really sorry for the inconvenience that you get the text but your account secure no need to worry”.
I pressed on and tried to make them understand that someone was up to something and wanted some sort of escalation. Then our CTO, who holds a breadth of experience consulting for a number of telecommunications companies and a plethora of others, voiced “isn’t this all too convenient with your mortgage about to come through? Do these guys know the exact time to strike before the funds hit your bank account and close just before end of day?” This was enough to start the heart racing.
Lodging a complaint appeared to be the only way to do any kind of escalation
Which is not what you want to hear when you feel the shadow of identity theft creeping over you. So what do you do? Yell at the poor chat representative? Get on the phone to start 30 minutes of hold time? I agreed to the complaint and then was surprised that I didn’t even get to word it. I was told ‘[the complaint] has been submitted on your behalf’.
I was then transferred to a dedicated team on chat for account unlocks as I still couldn’t login to my account and had yet to receive the recovery password.
Great, now what? I sent an update to my wife that I suspected someone was trying to steal my identity.
The plot thickens…
She immediately responded with a screenshot from her phone of this message, and asked if it was me who had gotten access to her phone account:
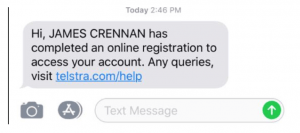
I should clarify the time stamps here: my phone is set to Japan Standard Time for these screenshots, which is two hours behind my wife’s phone, which is set at Australian Eastern Standard Time.
This threw me into a bit of a panic as it dawned on us that someone had attained access to my account successfully, knew who I was married to and then somehow got my Telco to add them as an administrator to her account without her input. More pieces of the identity puzzle attained by the culprit. My wife called our telco straight away and was directed to fill out an online fraud form and submit it, then wait for a response – not something we felt was exactly urgent enough.
Port-out scam enacted
I was still on my support chat, and as I chatted I received this notification that my phone number was being transferred away:
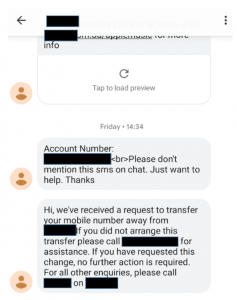
This last message is received at 15.10pm JST (I have a Google Pixel, so timestamps are only done with a decent lag).
The concurrent chat transcript I went through with my telco is below, and yes I did break out the caps lock:
I was a quite angry at this point, probably not thinking clearly and was quite certain that the billing department was not going to be able to help me.
Let’s recap the sequence of events so far:
- 12.05pm JST: a verification code was sent to my mobile.
- 12.46pm JST: my account registers to access my wife’s account successfully.
- 12.52pm JST: another verification code was sent to my mobile (gained from ‘more info’ from the second email in the first screenshot shown in this blog).
- 14.34pm JST: a chat rep gives my account number to the culprit via SMS to my mobile number (and what other mobile numbers?).
- 15.10pm JST: notification received of phone number being transferred away.
I of course dialed the number provided by the phone number transfer SMS (but redacted to protect the identity of the Telco) to try and halt the phone number theft. In the meantime, billing did a pretty great job of sending me to the right place:

Then you start thinking: these guys are good. How many apps do I have with 2FA? Could they pull the same personality imitation with my bank now they can provide SMS verification?
These are thoughts that turn your blood to ice. And they are targeting you.
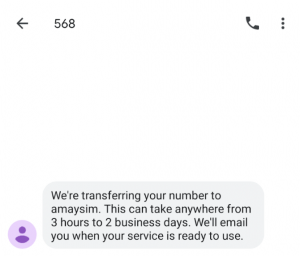
Moving as fast as I could with the team on the phone, they assured me that they would stop the number leaving my control… Then my phone informed me that I had lost my number and my phone service, but not before Amaysim sent me an SMS to politely to let me know my number was moving to their service:
I was told on the phone that I needed to submit a form, so I printed it, filled it in by hand, scanned it and emailed it back while concurrently breaking a land-speed record running around our Tokyo office. Imagine if you were not in a position to print, sign, scan? Like at an airport? I then had no choice but to wait and pray they enacted the form fast enough to stop the number transfer.
On the online chat support, I was now on my 4th representative, having moved through support, password resets, billing, and now back to support and was dealing with someone that started typing with authority. Throughout this whole process I had still not able to login to my account through a manual reset with the chat representatives because they were sending resets to an email address I hadn’t logged into in years: a Hotmail address, despite repeated requests to send it to a current gmail address.
I tried and failed to login to the old Hotmail address. Clicking on the password reset button, it notified me that, you guessed it, ‘we a have sent a SMS verification code to your mobile. Please enter the 6 digit code to reset your password’. It really starts to dawn on you how reliant you are on a phone number for online accounts.
No doubt exasperated, the lady with authority that I was chatting to all of a sudden pasted into the (non-encrypted) chat:
- USERNAME: XXXXXXXX
- PASSWORD: XXXXXXXXX
… and told me to login with this and change my account details. It’s important to note that up until this point in time, the only information I had given this stream of chat representatives was:
- My full name;
- My date of birth; and
- My mobile number (that I no longer had access to).
I literally needed less information than the scammer had needed to hack back into my own account.
My telco had simply believed me, without even confirming anything via voice, that I was who I said I was.
After changing all my account details, I called my bank and before I had even proven my identity, I gave them my customer ID and they froze my accounts, which is also a bit worrying. This really should have been my first step in an identity compromise triage process. After my accounts were frozen while I was on hold, I logged in, and found that our bank accounts had a virtual zero value.
It hit me like a freight train
Despite being a veteran who served in combat operations, I started to experience a physiological response like nothing I have ever felt before. I was shaking so hard that I couldn’t type. I understood the term ‘white-hot rage’. I did my best to control my voice and asked two of my colleagues alongside me at the time to give me the room. Then I put my face in my trembling hands. Missing a settlement date for a property purchase in Australia sees interest charges apply. Missing a settlement by 14 days sees your 10% deposit lost to the seller, and you must re-negotiate to buy the property anew.
Did I just watch my family’s future slip through my fingers?
As the bank came back from hold to tell me my accounts were frozen, I told them it was too late. Not hearing their next sentences over the phone, I sent a message to my wife telling her I was too late, that I should have prioritized what was important and I hadn’t stopped them getting to our bank accounts.
My wife, like Gandalf on the dawn of the Helms Deep battle
…tells me that she had preemptively thought they would go for our bank funds, and so had called the bank to transfer everything to a temporary holding account. I can’t remember exactly, but I think I collapsed into a puddle of relief on top of my Macbook and sent her 1 google love heart emoji’s over Facebook Messenger chat.
In the meantime, she had gone through a much harder battle getting into her telco account over the phone, as they held her to a much higher identity proof regime and her date of birth was listed incorrectly. But she got there in the end after a similar process of grinding them down over an hour of dogged determination.
An hour later, my phone number was returned to me. After consulting with one of our cyber experts with a Masters in Cybersecurity from Brown University, I started my process to become a hard target. I’ll explain these steps below, but first let me define a port-out scam from on objective stand point, in consultation with our Data Protection Officer.
What is a port-out scam?
Essentially, a port-out scam involves a scammer acting as you in either a phone branch, via a phone call, or via your phone provider’s live chat and providing a comically weak set of security questions to gain access to your account. Then, they ask to move your phone number to another provider or change your SIM card.
What does this mean?
It means that all your verification messages for services such as banking, software account access and the like would be in the hands of someone with malicious intent.
What is preventing them from being able to do this to you right now?
Depending on your provider, they may only need to provide as little as this information to convince your telco provider they are you and get access to the what we can call the “first tier” of your account privileges:
- Your full name;
- Your date of birth; and
- Your mobile number.
Obviously, this information could be found in 2 internet searches, and may be all accessible on either your LinkedIn or your Facebook profile.
To make more substantial requests, such as changing your login details, moving your phone number or other the like, you will likely have to receive a text with a verification code that needs to be read back or typed into chat, and you get access to “second tier” privileges.
But, what if your phone is stolen or lost? You can usually still get the full second tier access by providing other information that should be hard to come by, such as your account number, what your previous bill was, the branch you purchased your phone in, billing address etc.
What is silly about this information verification step for the second tier is that you can likely get the answers with innocent questions once you have cleared the first tier. Questions such as “I just wanted to check on my last bill? Thanks for that – oh, and while I have just you on the line, what was my account number again? I had it written down somewhere before…” If this additional information is indeed held secure, which it should be, then this is where the big dupe comes in. Begging the chat representative to help them get access because they are in a dire situation about to miss their plane home, or they have a crying baby (and are playing a youtube video of a crying baby at 150 decibels in the background) and the sky is falling, or any other urgent reason, appeals to sympathy and tempts them to break security protocol. The crying baby is no joke! See the youtube video below:
A variant of this style of people pressuring is what I believe happened in my instance, and led to what I think could have been a coordinated attempt to clean out my bank in the few hours it would hold my mortgage drawings.
What should you do?
I believe the majority that will read this are users of software and generally vigilant when it comes to security for their work. But it’s really easy in a busy job to forget about vigilance with your own personal accounts and just do things that maximize convenience… An XKCD comic comes to mind:
After reviewing the what’s available on port-out scams and consulting with further security experts, here is our advice on how to best protect yourself from something similar:
Be a hard target.
At the end of the day, nothing is totally secure, but you can adhere to the ‘hard target’ principal of being harder than the next person to target. This hopefully creates a deterrent from being selected from an initial screening as a prospect that is likely to result in easy infiltration (probability of successful hack). |
 |
Epilogue
Having spoken to an investigator for my telco since then, it seems that ‘mobile mobility laws’ in my country (Australia) have yet to catch up to scammer tactics – and regulation is being actively lobbied to be changed by the telcos to augment security… In the US, you can at least request PIN protection on this process, but you need to voluntarily request to do this. I believe the same is true for Europe.
I was also informed that connecting to a bad public wifi source may be the trigger that got me into trouble in the first place in Tokyo. This has yet to be confirmed but is alarming considering Tokyo is arguably the safest city in the world. If you have the ‘connect to any public wifi source’ option on your phone (Pixels have this and is a non-default option), I recommend disabling it and using a VPN anytime you're on a public wi-fi network.
Our business security practices at DreamFactory have always been pretty strict, but I hadn’t gone to the effort of applying the same rigor to my personal web presence. I have since upgraded all my personal security, and family’s security, in line with these recommendations, and I strongly urge you to take some precautions to become a harder target. Had I not been on the front foot early and in a good position to be able to focus on shutting down this scam, who knows how far they would have gone.
In summary, please:
-
be a hard target; and
- act early on warning signs.
TeamPassword guest blogger James Crennan is a Principal at Xenon Partners, and former CEO of DreamFactory Software.